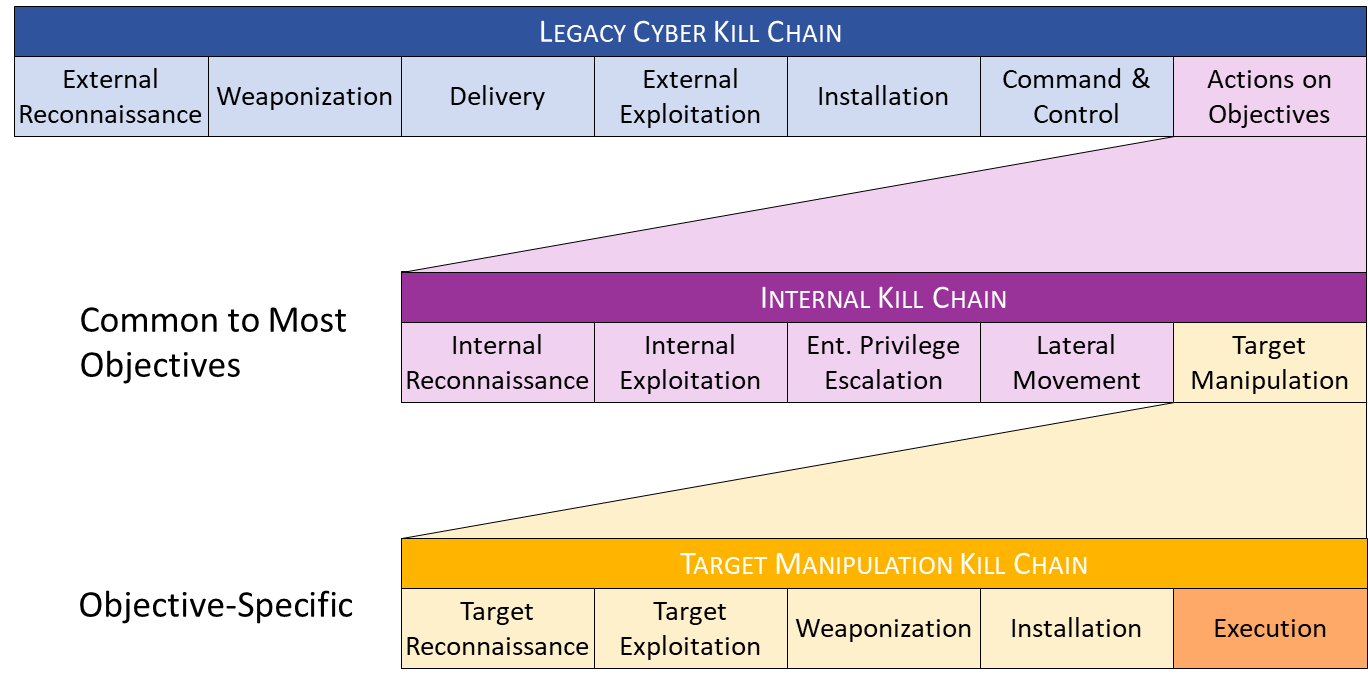
Building on the Legacy Cyber Kill Chain, this model includes the new Internal Kill Chain and Target Manipulation Kill Chain. This model highlights opportunities to detect and frustrate the adversary at every stage. Don’t declare “GAME OVER” just because the adversary has breached the perimeter!
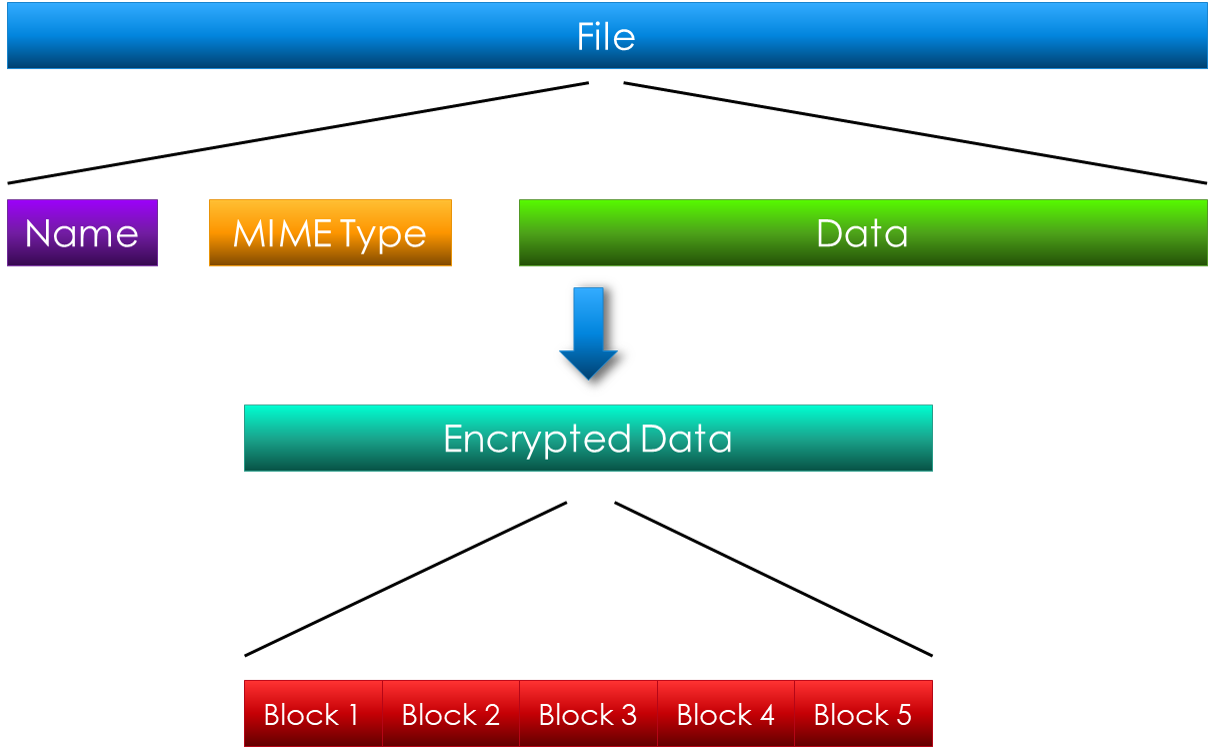
Some data is too sensitive or volatile to store on systems you own. What if we could store it somewhere else without compromising the security or availability of the data, while leveraging intended functionality to do so? This software creates a distributed file store built on top of a JavaScript botnet. This type of data storage offers redundancy & encryption and allows you to store a virtually unlimited amount of data in any type of file. They can seize your server — but the data’s not there!

A presentation at BSides Seattle 2012 providing advice for accelerating a career in information security.
A proposal for a new hash algorithm, developed at Sandia National Laboratories and submitted to the NIST SHA3 competition.
An extension of the Java BufferedReader class to prevent DoS attacks from large files with no line breaks.